Ethereum’s Founder, Vitalik Buterin, recently shared a post delving into the intricate technical challenges associated with establishing seamless communication and data accessibility across distinct layers of blockchain infrastructure.
In the spotlight of Buterin’s discussion was the need to facilitate data reading between a parent chain or layer-one (L1) and its corresponding scaling solution or layer-two (L2), from L2 back to L1, and amidst various L2 solutions.
The Momentum of Layer 2 Scaling Solutions
The ascent of Layer 2 scaling solutions has been remarkable over the past months, with the foremost L2s amassing an impressive $9.38 billion in Total Value Locked (TVL).
Buterin contends that as these solutions continue to gain traction and smart contract wallets are increasingly employed, an evident gap arises that necessitates resolution.
The challenge emanates from the need for users managing assets across numerous layer-2s within smart contract wallets to manage key changes efficiently.
One proposed remedy in the post revolves around the adoption of counterfactual addresses. Smart contract wallets can employ counterfactual addresses, which remain off-chain, to receive and retain assets. This is facilitated by the CREATE2 functionality, which empowers the generation of an Ethereum address.
Furthermore, the post introduced the notion of an asset/keystore separation architecture, facilitating key changes for users within a multi-L2 environment. This architecture was dissected into two implementations: a light version and a heavy version.
While the former entails wallets locally storing keys and periodically verifying proofs to update them, the latter necessitates cross-chain proofs for each transaction, subsequently authenticating keys in the keystore.
Ethereum State Root
Cross-chain proofs substantiate transactions between diverse blockchain networks or layers. In scenarios where the wallet and keystore reside on different layer-2 (L2) networks, a comprehensive cross-chain proof for wallet keys comprises two pivotal components.
Firstly, a validation proof verifies the present state of the keystore-holding L2 network using the Ethereum state root known to the wallet-holding L2 network. Secondly, a proof illustrates the existence of current keys within the keystore by leveraging the state root of the keystore-holding L2 network.
Buterin delineated five distinct cross-chain proof methods: Merkle proofs, General-purpose ZK-SNARKs, Special-purpose proofs (e.g., with KZG), Verkle proofs, and No proofs (relying on direct state reading). These methods were ranked based on ease of implementation and cost using an illustrative chart.
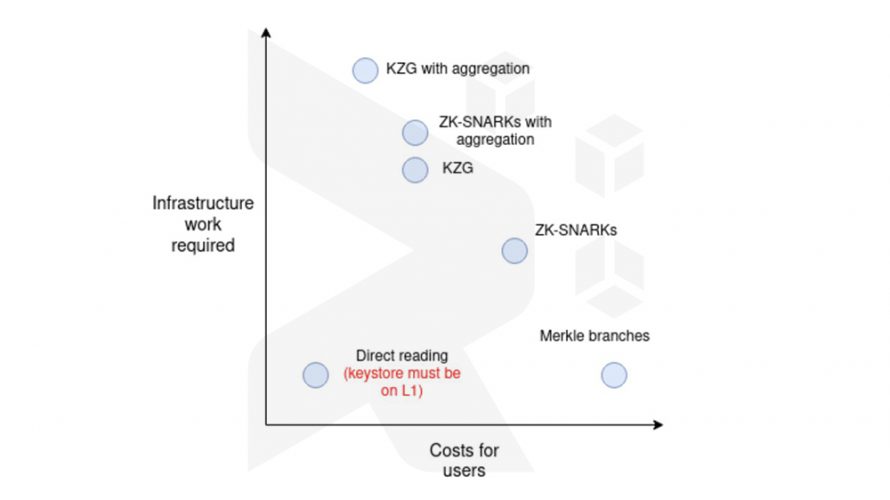
The report elaborated on the operational mechanisms of each approach and delineated the advantages and disadvantages of all the methods concerning gas expenditures, computational capacities, and data dimensions.
The conclusion drawn was that the selection of the method would predominantly hinge on the specific use case and the intended balance between gas utilization and network security.





